Cybersecurity Market Growth and Industry Forecast
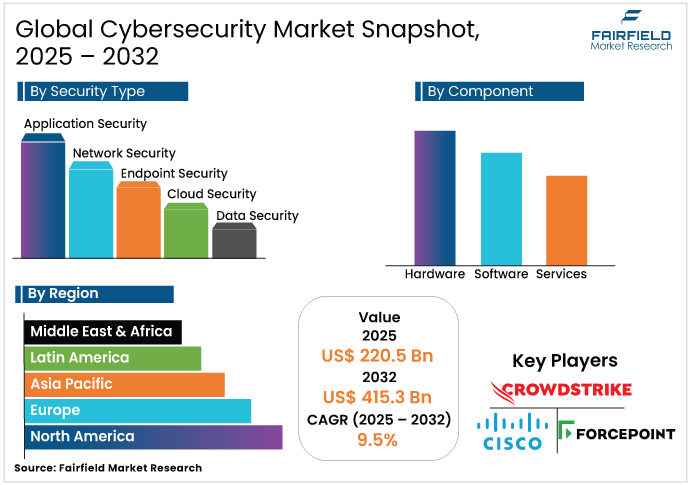
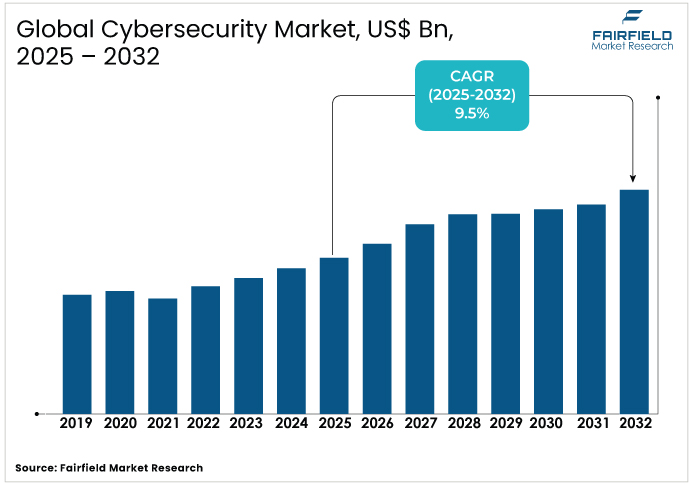
- The global cybersecurity market is projected to be valued at US$220.5 Bn in 2025.
- It is expected to grow at a CAGR of 9.5% from 2025 to 2032, reaching US$415.3 Bn by 2032.
Cybersecurity Market Summary Key Insights & Trends
- Software dominates by component, led by IAM, SIEM, and encryption adoption across enterprises.
- Services are the fastest-growing, with managed security and consulting in high demand amid talent shortages.
- Network security leads the cybersecurity market, while cloud security grows fastest, driven by increasing cloud adoption and remote work trends.
- On-premises deployment remains dominant, but cloud-based models expand rapidly with SME adoption and hybrid work.
- Large enterprises hold the largest share, while SMEs witness the fastest growth through managed service reliance.
- Government & defense led by industry, while healthcare grows fastest, fueled by IoT devices and HIPAA compliance.
- North America leads regionally, but Asia Pacific expands quickest, with a CAGR exceeding 2% through 2032.
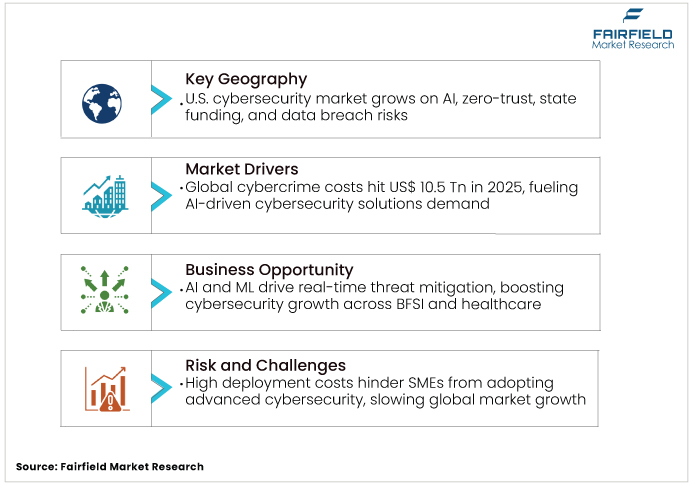
- Rising cybercrime costs of US$10.5 Tn in 2025 remain the strongest driver for advanced cybersecurity adoption.
A Look Back and a Look Forward - Comparative Analysis
The cybersecurity market witnessed substantial growth between 2019 and 2024, propelled by escalating cyber threats and the rapid pace of digital transformation. The COVID-19 pandemic accelerated this growth, as remote work surged by 87% in the U.S., expanding attack surfaces through in-home networks and devices. High-profile data breaches, such as those affecting Facebook and Marriott, underscored the need for robust cybersecurity solutions. Governments, such as the U.K., invested heavily (USD 2.3 billion in 2020) in network security, while the market faced challenges from a shortage of skilled professionals, with 663,000 unfilled U.S. cybersecurity positions in 2023. The adoption of AI and ML technologies began reshaping threat detection, setting the stage for future growth.
The cybersecurity industry is projected to expand steadily through 2032, fueled by rising cyber threats and continuous technological advancements. The proliferation of IoT devices (expected to exceed 75 billion by 2025) and cloud-based environments will expand attack surfaces, boosting demand for cloud and endpoint security. Regulatory compliance, such as the U.S. Cyber Trust Mark, will drive investments in secure IoT devices. AI and ML integration will enhance automated threat detection, while the Asia-Pacific region, led by China and India, will see the fastest growth due to rapid digitalization. The persistent skills gap, with 3.5 million unfilled roles globally, will challenge growth but spur opportunities for training and innovation.
Key Growth Drivers
- Growing Complexity of Cyber Threats Driving Advanced Cybersecurity Solutions Adoption
The cybersecurity market is driven by the increasing frequency and complexity of cyberattacks, such as ransomware, phishing, and zero-day vulnerabilities. In 2025, global cybercrime costs reached US$10.5 trillion annually, a 300% increase from 2015, highlighting the urgent need for advanced security solutions. Ransomware-as-a-Service (RaaS) has emerged as a key threat, targeting critical infrastructure and causing significant financial and operational damage. Organizations are investing heavily in AI-driven threat detection and response systems to counter these sophisticated attacks. For instance, Cisco’s HyperShield, launched in 2024, reduces response times from days to minutes using AI. The cybersecurity solutions benefit from this demand for proactive measures to protect sensitive data and ensure business continuity.
- Strict Global Regulations Fuel Cybersecurity Investments Across Key Industry Verticals
Stringent regulations such as GDPR, CCPA, and the U.S. Cyber Trust Mark (launched January 2025) are major drivers for the cybersecurity market. These frameworks mandate robust data protection, pushing organizations to invest in compliance-driven solutions. The UK Government's Cyber Security Breaches Survey 2024 reported a 22% of businesses and 14% of charities have been the victim of at least one cybercrime in the last 12 months. Compliance requirements in industries such as BFSI and healthcare drive demand for Identity and Access Management (IAM) and data security solutions. The cybersecurity industry sees growth as businesses adopt zero-trust architectures and encryption to meet regulatory standards, ensuring consumer trust and avoiding hefty fines.
- Cloud Expansion and Digital Shift Accelerate Demand for Cybersecurity Solutions
The rapid shift to cloud computing and digital platforms fuels the market. By 2025, the global cloud computing market is expected to reach US$738.2 billion, increasing the need for cloud-native security solutions. The rise of IoT (75 billion devices by 2025) and 5G technology expands attack surfaces, necessitating advanced industry measures such as network segmentation and endpoint protection. Hybrid work environments further amplify demand for secure remote access solutions. Companies such as Palo Alto Networks and Microsoft are innovating with cloud-based security platforms, driving market growth as organizations prioritize safeguarding digital assets.
Key Growth Restraints
- Global Cybersecurity Skills Gap Restrains Adoption of Advanced Security Solutions
The cybersecurity market faces a significant restraint due to a global shortage of skilled professionals, with over 3.5 million unfilled roles in 2025. According to Lightcast Quarterly Cybersecurity Talent Report, In Q3 2024, the U.S. had demand for 1,583,880 cybersecurity jobs but only 1,319,117 skilled workers, meeting 83% of demand and leaving a shortage of nearly 265,000 professionals. This gap limits organizations’ ability to implement and manage advanced security systems. The rapid evolution of cyber threats requires continuous training, increasing costs and operational challenges. Businesses struggle to maintain robust defenses without adequate expertise, impacting market expansion.
- Expensive Cybersecurity Deployments Challenge SMEs and Emerging Market Adoption
The high cost of deploying advanced cybersecurity solutions hinders market growth, particularly for SMEs. Implementing AI-driven tools, zero-trust architectures, and cloud security requires significant investment in hardware, software, and services. For instance, comprehensive security suites from vendors such as Palo Alto Networks can be cost-prohibitive for smaller firms. Ongoing maintenance and training further add to expenses, limiting adoption in cost-sensitive markets. This restraint slows the cybersecurity market’s penetration in emerging economies and smaller enterprises, despite growing cyber threats.
Cybersecurity Market Trends and Opportunities
- Artificial Intelligence and Machine Learning Revolutionize Cybersecurity Threat Detection
The integration of AI and ML into the cybersecurity market presents significant opportunities. These technologies enhance threat detection, predictive analytics, and automated response, reducing reliance on manual processes. AI-driven solutions, such as Cisco’s HyperShield, enable real-time threat mitigation, attracting businesses seeking efficient security. The cybersecurity industry can capitalize on this trend by developing innovative AI-powered tools, fostering growth in sectors such as BFSI and healthcare, where data protection is critical.
- Rapid Digitalization in Asia-Pacific Creates Expanding Cybersecurity Market Opportunities
Asia Pacific offers substantial opportunities for the market, driven by rapid digitalization in countries such as China, India, and Japan. The region is projected to achieve a CAGR of over 14.2% through 2032, fueled by increasing internet penetration and IoT adoption. Thailand’s goal to expand its digital economy to 30% of GDP by 2030 highlights the region’s focus on cybersecurity. Investments in smart cities and 5G infrastructure create demand for advanced security solutions.
Segment-wise Trends & Analysis
- Software Holds the Lead While Services Segment Records Fastest Expansion
The software segment dominates by holding the largest share in 2024 due to the widespread adoption of security solutions such as firewalls, antivirus, and IAM tools. Enterprises rely on software for real-time threat detection and compliance management, with companies such as Microsoft and IBM leading innovation. The services segment, including managed security services, is the fastest-growing, driven by the need for expert-led solutions amid a skills shortage. Services are expected to see strong growth, driven by rising demand for incident response and consulting, which plays a crucial role in strengthening cybersecurity market resilience.
- Network Protection Dominates While Cloud-Based Security Solutions Grow Rapidly
Network security leads the market, accounting for a 28.6% revenue share in 2024, driven by the need to protect critical IT infrastructure from cyberattacks. Solutions such as firewalls and VPNs are critical for industries such as BFSI and government. Cloud security is the fastest-growing segment due to the rapid adoption of cloud services, remote work, and increasing cyber threats targeting cloud-based infrastructure and data. The cybersecurity industry benefits from innovations such as Cisco’s HyperShield, addressing vulnerabilities in cloud-based environments and ensuring robust protection.
- On Premises Preferred by Large Enterprises While Cloud Adoption Accelerates
On-premises deployment leads, favored by large enterprises for its control and customization, particularly in BFSI and government sectors. In 2024, it held a significant market share due to its reliability for sensitive data. Cloud-based deployment is the fastest-growing, driven by scalable and cost-effective solutions for SMEs and hybrid work environments. The industry is witnessing greater adoption of cloud-native protection solutions, supported by steady double-digit growth through 2032, highlighting the ongoing shift toward digital platforms.
- Large Organizations Lead the Way While SMEs Witness Fastest Growth
Large enterprises dominate, holding the largest share in 2024 due to their extensive digital infrastructure and regulatory compliance needs. Companies such as Palo Alto Networks cater to this segment with comprehensive security suites. SMEs are the fastest-growing segment, driven by increasing cyber threats and affordable cloud-based solutions. Small and medium-sized enterprises are increasingly turning to managed services to address the skills shortage, driving steady double-digit growth through 2032 and broadening overall adoption.
- Government and Defense Sector Leads While Healthcare Emerges as Fastest Growing Segment
The government and defense sector leads, capturing a 28.6% share in 2025, driven by heavy investments in national cybersecurity, such as the U.S. Department of Treasury’s US$20 billion PROTECTS vehicle. Healthcare is the fastest-growing segment, fueled by the rise in IoT-enabled medical devices and regulatory requirements such as HIPAA. In 2025, healthcare’s demand for data security solutions, such as Atlas Systems’ ComplyScore, drives rapid cybersecurity market growth, with a projected CAGR of 14% through 2032.
Regional Trends & Analysis
- North America Leads Through Strong Digital Infrastructure and Robust Regulations
North America leads as the U.S cybersecurity market is driven by advanced digital infrastructure and regulatory frameworks such as the cyber trust mark. More than 1.7 billion data breach notices were issued across the United States in 2024, according to a report from the Identity Theft Resource Center (ITRC), prompting investments in zero-trust and AI-driven solutions. In H1 2025 alone, California startups raised approximately $94.5 billion. In 2023, New York Governor Kathy Hochul added $35 million to the state’s $61.9 million cybersecurity budget and created a new team focused on protecting critical infrastructure, both of which are fueling market growth.
- Europe Strengthens Position with Regulatory Standards and Rising Security Investments
Europe holds a 25.1% cybersecurity industry share in 2025, led by the U.K. and Germany. The U.K.’s cybersecurity sector generated US$17.5 billion in 2024, driven by a 12% rise in cyber incidents and NCSC initiatives. Germany aligns with EU Cybersecurity Act standards, with firms such as SAP deploying AI-powered solutions for Industry 4.0. The market in Europe grows through government-backed research and regulatory compliance, addressing ransomware and data breaches in BFSI and manufacturing.
- Asia Pacific Expands Rapidly Through Digitalization Smart Initiatives and IoT Adoption
Asia-Pacific is the fastest-growing, with a CAGR exceeding 14.2% through 2032, led by China, India, and Japan. China’s rapid digitalization and India’s increasing internet penetration drive demand for cloud and IoT security. Japan’s focus on smart cities and Thailand’s digital economy goals (30% of GDP by 2030) fuel investments in network security.
Competitive Landscape
The cybersecurity market is highly competitive, with key players such as Cisco, Palo Alto Networks, and Microsoft leveraging AI, ML, and strategic acquisitions to maintain dominance. Companies focus on unified security suites to reduce complexity, while startups such as Wiz innovate in cloud security. Vendors are prioritizing research, development, and strategic partnerships to counter evolving digital threats.
Key Companies
- Forcepoint
- Cisco Systems
- CrowdStrike
- Trend Micro Incorporated
- Sophos Ltd.
- IBM Corporation
- FireEye
- Palo Alto Networks
- Microsoft
- Juniper Networks
- Broadcom
- Fortinet
- McAfee
- Check Point Software Technologies
Recent Industry Developments
- In June 2025 (specifically, June 4th), Microsoft announced a new European Security Program (ESP), which offers free AI-powered cybersecurity support to European governments in response to escalating state-sponsored cyber threats, particularly from nations such as Russia, China, Iran, and North Korea
- In May 2024, Cisco unveiled the initial integration of Splunk technology into its security products, including enhancing its XDR solution with Splunk analytics for AI-driven threat detection and response.
Global Cybersecurity Market Segmentation
By Component:
- Hardware
- Firewall Appliance
- Security Routers & Gateways
- DDoS Mitigation Appliances
- Hardware Security Modules (HSM)
- IDS/IPS
- Others
- Software
- Identity & Access Management (IAM) Software
- Data Loss Prevention Software
- Encryption Software
- Security Information & Event Management (SIEM)
- Extended Detection & Response (XDR)
- Others
- Services
- Professional Services
- Implementation and Integration
- Security Consulting & Advisory Services
- Incident Response & Forensics
- Compliance Readiness & Certification Support
- Others
- Managed Services
By Security Type:
- Application Security
- Network Security
- Endpoint Security
- Cloud Security
- Data Security
- Others
By Deployment:
- Cloud-based
- Hybrid
- On-premises
By Enterprise Size:
- Small & Medium-sized Enterprise (SMEs)
- Large Enterprise
By Industry:
- IT & Telecom
- Retail & E-commerce
- BFSI
- Government
- Manufacturing
- Energy and Utilities
- Healthcare
- Aerospace & Defense
- Transportation and Logistics
- Others
By Region
- North America
- Europe
- Asia Pacific
- Latin America
- Middle East & Africa
1. Executive Summary
1.1. Global Cybersecurity Market Snapshot
1.2. Future Projections
1.3. Key Market Trends
1.4. Regional Snapshot, by Value, 2025
1.5. Analyst Recommendations
2. Market Overview
2.1. Market Definitions and Segmentations
2.2. Market Dynamics
2.2.1. Drivers
2.2.2. Restraints
2.2.3. Market Opportunities
2.3. Value Chain Analysis
2.4. COVID-19 Impact Analysis
2.5. Porter's Fiver Forces Analysis
2.6. Impact of Russia-Ukraine Conflict
2.7. PESTLE Analysis
2.8. Regulatory Analysis
2.9. Price Trend Analysis
2.9.1. Current Prices and Future Projections, 2024-2032
2.9.2. Price Impact Factors
3. Global Cybersecurity Market Outlook, 2019 - 2032
3.1. Global Cybersecurity Market Outlook, by Component, Value (US$ Bn), 2019 - 2032
3.1.1. Hardware
3.1.1.1. Firewall Appliance
3.1.1.2. Security Routers & Gateways
3.1.1.3. DDoS Mitigation Appliances
3.1.1.4. Hardware Security Modules (HSM)
3.1.1.5. IDS/IPS
3.1.1.6. Others
3.1.2. Software
3.1.2.1. Identity & Access Management (IAM) Software
3.1.2.2. Data Loss Prevention Software
3.1.2.3. Encryption Software
3.1.2.4. Security Information & Event Management (SIEM)
3.1.2.5. Extended Detection & Response (XDR)
3.1.2.6. Others
3.1.3. Services
3.1.3.1. Professional Services
3.1.3.2. Managed Services
3.2. Global Cybersecurity Market Outlook, by Security Type, Value (US$ Bn), 2019 - 2032
3.2.1. Application Security
3.2.2. Network Security
3.2.3. Endpoint Security
3.2.4. Cloud Security
3.2.5. Data Security
3.2.6. Others
3.3. Global Cybersecurity Market Outlook, by Deployment, Value (US$ Bn), 2019 - 2032
3.3.1. Cloud-based
3.3.2. Hybrid
3.3.3. On-premises
3.4. Global Cybersecurity Market Outlook, by Enterprise Size, Value (US$ Bn), 2019 - 2032
3.4.1. Small & Medium-sized Enterprise (SMEs)
3.4.2. Large Enterprise
3.5. Global Cybersecurity Market Outlook, by Industry, Value (US$ Bn), 2019 - 2032
3.5.1. IT & Telecom
3.5.2. Retail & E-commerce
3.5.3. BFSI
3.5.4. Government
3.5.5. Manufacturing
3.5.6. Energy and Utilities
3.5.7. Healthcare
3.5.8. Aerospace & Defense
3.5.9. Transportation and Logistics
3.5.10. Others
3.6. Global Cybersecurity Market Outlook, by Region, Value (US$ Bn), 2019 - 2032
3.6.1. North America
3.6.2. Europe
3.6.3. Asia Pacific
3.6.4. Latin America
3.6.5. Middle East & Africa
4. North America Cybersecurity Market Outlook, 2019 - 2032
4.1. North America Cybersecurity Market Outlook, by Component, Value (US$ Bn), 2019 - 2032
4.1.1. Hardware
4.1.1.1. Firewall Appliance
4.1.1.2. Security Routers & Gateways
4.1.1.3. DDoS Mitigation Appliances
4.1.1.4. Hardware Security Modules (HSM)
4.1.1.5. IDS/IPS
4.1.1.6. Others
4.1.2. Software
4.1.2.1. Identity & Access Management (IAM) Software
4.1.2.2. Data Loss Prevention Software
4.1.2.3. Encryption Software
4.1.2.4. Security Information & Event Management (SIEM)
4.1.2.5. Extended Detection & Response (XDR)
4.1.2.6. Others
4.1.3. Services
4.1.3.1. Professional Services
4.1.3.2. Managed Services
4.2. North America Cybersecurity Market Outlook, by Security Type, Value (US$ Bn), 2019 - 2032
4.2.1. Application Security
4.2.2. Network Security
4.2.3. Endpoint Security
4.2.4. Cloud Security
4.2.5. Data Security
4.2.6. Others
4.3. North America Cybersecurity Market Outlook, by Deployment, Value (US$ Bn), 2019 - 2032
4.3.1. Cloud-based
4.3.2. Hybrid
4.3.3. On-premises
4.4. North America Cybersecurity Market Outlook, by Enterprise Size, Value (US$ Bn), 2019 - 2032
4.4.1. Small & Medium-sized Enterprise (SMEs)
4.4.2. Large Enterprise
4.5. North America Cybersecurity Market Outlook, by Industry, Value (US$ Bn), 2019 - 2032
4.5.1. IT & Telecom
4.5.2. Retail & E-commerce
4.5.3. BFSI
4.5.4. Government
4.5.5. Manufacturing
4.5.6. Energy and Utilities
4.5.7. Healthcare
4.5.8. Aerospace & Defense
4.5.9. Transportation and Logistics
4.5.10. Others
4.6. North America Cybersecurity Market Outlook, by Country, Value (US$ Bn), 2019 - 2032
4.6.1. U.S. Cybersecurity Market Outlook, by Component, 2019 - 2032
4.6.2. U.S. Cybersecurity Market Outlook, by Security Type, 2019 - 2032
4.6.3. U.S. Cybersecurity Market Outlook, by Deployment, 2019 - 2032
4.6.4. U.S. Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
4.6.5. U.S. Cybersecurity Market Outlook, by Industry, 2019 - 2032
4.6.6. Canada Cybersecurity Market Outlook, by Component, 2019 - 2032
4.6.7. Canada Cybersecurity Market Outlook, by Security Type, 2019 - 2032
4.6.8. Canada Cybersecurity Market Outlook, by Deployment, 2019 - 2032
4.6.9. Canada Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
4.6.10. Canada Cybersecurity Market Outlook, by Industry, 2019 - 2032
4.7. BPS Analysis/Market Attractiveness Analysis
5. Europe Cybersecurity Market Outlook, 2019 - 2032
5.1. Europe Cybersecurity Market Outlook, by Component, Value (US$ Bn), 2019 - 2032
5.1.1. Hardware
5.1.1.1. Firewall Appliance
5.1.1.2. Security Routers & Gateways
5.1.1.3. DDoS Mitigation Appliances
5.1.1.4. Hardware Security Modules (HSM)
5.1.1.5. IDS/IPS
5.1.1.6. Others
5.1.2. Software
5.1.2.1. Identity & Access Management (IAM) Software
5.1.2.2. Data Loss Prevention Software
5.1.2.3. Encryption Software
5.1.2.4. Security Information & Event Management (SIEM)
5.1.2.5. Extended Detection & Response (XDR)
5.1.2.6. Others
5.1.3. Services
5.1.3.1. Professional Services
5.1.3.2. Managed Services
5.2. Europe Cybersecurity Market Outlook, by Security Type, Value (US$ Bn), 2019 - 2032
5.2.1. Application Security
5.2.2. Network Security
5.2.3. Endpoint Security
5.2.4. Cloud Security
5.2.5. Data Security
5.2.6. Others
5.3. Europe Cybersecurity Market Outlook, by Deployment, Value (US$ Bn), 2019 - 2032
5.3.1. Cloud-based
5.3.2. Hybrid
5.3.3. On-premises
5.4. Europe Cybersecurity Market Outlook, by Enterprise Size, Value (US$ Bn), 2019 - 2032
5.4.1. Small & Medium-sized Enterprise (SMEs)
5.4.2. Large Enterprise
5.5. Europe Cybersecurity Market Outlook, by Industry, Value (US$ Bn), 2019 - 2032
5.5.1. IT & Telecom
5.5.2. Retail & E-commerce
5.5.3. BFSI
5.5.4. Government
5.5.5. Manufacturing
5.5.6. Energy and Utilities
5.5.7. Healthcare
5.5.8. Aerospace & Defense
5.5.9. Transportation and Logistics
5.5.10. Others
5.6. Europe Cybersecurity Market Outlook, by Country, Value (US$ Bn), 2019 - 2032
5.6.1. Germany Cybersecurity Market Outlook, by Component, 2019 - 2032
5.6.2. Germany Cybersecurity Market Outlook, by Security Type, 2019 - 2032
5.6.3. Germany Cybersecurity Market Outlook, by Deployment, 2019 - 2032
5.6.4. Germany Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
5.6.5. Germany Cybersecurity Market Outlook, by Industry, 2019 - 2032
5.6.6. Italy Cybersecurity Market Outlook, by Component, 2019 - 2032
5.6.7. Italy Cybersecurity Market Outlook, by Security Type, 2019 - 2032
5.6.8. Italy Cybersecurity Market Outlook, by Deployment, 2019 - 2032
5.6.9. Italy Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
5.6.10. Italy Cybersecurity Market Outlook, by Industry, 2019 - 2032
5.6.11. France Cybersecurity Market Outlook, by Component, 2019 - 2032
5.6.12. France Cybersecurity Market Outlook, by Security Type, 2019 - 2032
5.6.13. France Cybersecurity Market Outlook, by Deployment, 2019 - 2032
5.6.14. France Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
5.6.15. France Cybersecurity Market Outlook, by Industry, 2019 - 2032
5.6.16. U.K. Cybersecurity Market Outlook, by Component, 2019 - 2032
5.6.17. U.K. Cybersecurity Market Outlook, by Security Type, 2019 - 2032
5.6.18. U.K. Cybersecurity Market Outlook, by Deployment, 2019 - 2032
5.6.19. U.K. Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
5.6.20. U.K. Cybersecurity Market Outlook, by Industry, 2019 - 2032
5.6.21. Spain Cybersecurity Market Outlook, by Component, 2019 - 2032
5.6.22. Spain Cybersecurity Market Outlook, by Security Type, 2019 - 2032
5.6.23. Spain Cybersecurity Market Outlook, by Deployment, 2019 - 2032
5.6.24. Spain Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
5.6.25. Spain Cybersecurity Market Outlook, by Industry, 2019 - 2032
5.6.26. Russia Cybersecurity Market Outlook, by Component, 2019 - 2032
5.6.27. Russia Cybersecurity Market Outlook, by Security Type, 2019 - 2032
5.6.28. Russia Cybersecurity Market Outlook, by Deployment, 2019 - 2032
5.6.29. Russia Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
5.6.30. Russia Cybersecurity Market Outlook, by Industry, 2019 - 2032
5.6.31. Rest of Europe Cybersecurity Market Outlook, by Component, 2019 - 2032
5.6.32. Rest of Europe Cybersecurity Market Outlook, by Security Type, 2019 - 2032
5.6.33. Rest of Europe Cybersecurity Market Outlook, by Deployment, 2019 - 2032
5.6.34. Rest of Europe Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
5.6.35. Rest of Europe Cybersecurity Market Outlook, by Industry, 2019 - 2032
5.7. BPS Analysis/Market Attractiveness Analysis
6. Asia Pacific Cybersecurity Market Outlook, 2019 - 2032
6.1. Asia Pacific Cybersecurity Market Outlook, by Component, Value (US$ Bn), 2019 - 2032
6.1.1. Hardware
6.1.1.1. Firewall Appliance
6.1.1.2. Security Routers & Gateways
6.1.1.3. DDoS Mitigation Appliances
6.1.1.4. Hardware Security Modules (HSM)
6.1.1.5. IDS/IPS
6.1.1.6. Others
6.1.2. Software
6.1.2.1. Identity & Access Management (IAM) Software
6.1.2.2. Data Loss Prevention Software
6.1.2.3. Encryption Software
6.1.2.4. Security Information & Event Management (SIEM)
6.1.2.5. Extended Detection & Response (XDR)
6.1.2.6. Others
6.1.3. Services
6.1.3.1. Professional Services
6.1.3.2. Managed Services
6.2. Asia Pacific Cybersecurity Market Outlook, by Security Type, Value (US$ Bn), 2019 - 2032
6.2.1. Application Security
6.2.2. Network Security
6.2.3. Endpoint Security
6.2.4. Cloud Security
6.2.5. Data Security
6.2.6. Others
6.3. Asia Pacific Cybersecurity Market Outlook, by Deployment, Value (US$ Bn), 2019 - 2032
6.3.1. Cloud-based
6.3.2. Hybrid
6.3.3. On-premises
6.4. Asia Pacific Cybersecurity Market Outlook, by Enterprise Size, Value (US$ Bn), 2019 - 2032
6.4.1. Small & Medium-sized Enterprise (SMEs)
6.4.2. Large Enterprise
6.5. Asia Pacific Cybersecurity Market Outlook, by Industry, Value (US$ Bn), 2019 - 2032
6.5.1. IT & Telecom
6.5.2. Retail & E-commerce
6.5.3. BFSI
6.5.4. Government
6.5.5. Manufacturing
6.5.6. Energy and Utilities
6.5.7. Healthcare
6.5.8. Aerospace & Defense
6.5.9. Transportation and Logistics
6.5.10. Others
6.6. Asia Pacific Cybersecurity Market Outlook, by Country, Value (US$ Bn), 2019 - 2032
6.6.1. China Cybersecurity Market Outlook, by Component, 2019 - 2032
6.6.2. China Cybersecurity Market Outlook, by Security Type, 2019 - 2032
6.6.3. China Cybersecurity Market Outlook, by Deployment, 2019 - 2032
6.6.4. China Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
6.6.5. China Cybersecurity Market Outlook, by Industry, 2019 - 2032
6.6.6. Japan Cybersecurity Market Outlook, by Component, 2019 - 2032
6.6.7. Japan Cybersecurity Market Outlook, by Security Type, 2019 - 2032
6.6.8. Japan Cybersecurity Market Outlook, by Deployment, 2019 - 2032
6.6.9. Japan Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
6.6.10. Japan Cybersecurity Market Outlook, by Industry, 2019 - 2032
6.6.11. South Korea Cybersecurity Market Outlook, by Component, 2019 - 2032
6.6.12. South Korea Cybersecurity Market Outlook, by Security Type, 2019 - 2032
6.6.13. South Korea Cybersecurity Market Outlook, by Deployment, 2019 - 2032
6.6.14. South Korea Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
6.6.15. South Korea Cybersecurity Market Outlook, by Industry, 2019 - 2032
6.6.16. India Cybersecurity Market Outlook, by Component, 2019 - 2032
6.6.17. India Cybersecurity Market Outlook, by Security Type, 2019 - 2032
6.6.18. India Cybersecurity Market Outlook, by Deployment, 2019 - 2032
6.6.19. India Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
6.6.20. India Cybersecurity Market Outlook, by Industry, 2019 - 2032
6.6.21. Southeast Asia Cybersecurity Market Outlook, by Component, 2019 - 2032
6.6.22. Southeast Asia Cybersecurity Market Outlook, by Security Type, 2019 - 2032
6.6.23. Southeast Asia Cybersecurity Market Outlook, by Deployment, 2019 - 2032
6.6.24. Southeast Asia Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
6.6.25. Southeast Asia Cybersecurity Market Outlook, by Industry, 2019 - 2032
6.6.26. Rest of SAO Cybersecurity Market Outlook, by Component, 2019 - 2032
6.6.27. Rest of SAO Cybersecurity Market Outlook, by Security Type, 2019 - 2032
6.6.28. Rest of SAO Cybersecurity Market Outlook, by Deployment, 2019 - 2032
6.6.29. Rest of SAO Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
6.6.30. Rest of SAO Cybersecurity Market Outlook, by Industry, 2019 - 2032
6.7. BPS Analysis/Market Attractiveness Analysis
7. Latin America Cybersecurity Market Outlook, 2019 - 2032
7.1. Latin America Cybersecurity Market Outlook, by Component, Value (US$ Bn), 2019 - 2032
7.1.1. Hardware
7.1.1.1. Firewall Appliance
7.1.1.2. Security Routers & Gateways
7.1.1.3. DDoS Mitigation Appliances
7.1.1.4. Hardware Security Modules (HSM)
7.1.1.5. IDS/IPS
7.1.1.6. Others
7.1.2. Software
7.1.2.1. Identity & Access Management (IAM) Software
7.1.2.2. Data Loss Prevention Software
7.1.2.3. Encryption Software
7.1.2.4. Security Information & Event Management (SIEM)
7.1.2.5. Extended Detection & Response (XDR)
7.1.2.6. Others
7.1.3. Services
7.1.3.1. Professional Services
7.1.3.2. Managed Services
7.2. Latin America Cybersecurity Market Outlook, by Security Type, Value (US$ Bn), 2019 - 2032
7.2.1. Application Security
7.2.2. Network Security
7.2.3. Endpoint Security
7.2.4. Cloud Security
7.2.5. Data Security
7.2.6. Others
7.3. Latin America Cybersecurity Market Outlook, by Deployment, Value (US$ Bn), 2019 - 2032
7.3.1. Cloud-based
7.3.2. Hybrid
7.3.3. On-premises
7.4. Latin America Cybersecurity Market Outlook, by Enterprise Size, Value (US$ Bn), 2019 - 2032
7.4.1. Small & Medium-sized Enterprise (SMEs)
7.4.2. Large Enterprise
7.5. Latin America Cybersecurity Market Outlook, by Industry, Value (US$ Bn), 2019 - 2032
7.5.1. IT & Telecom
7.5.2. Retail & E-commerce
7.5.3. BFSI
7.5.4. Government
7.5.5. Manufacturing
7.5.6. Energy and Utilities
7.5.7. Healthcare
7.5.8. Aerospace & Defense
7.5.9. Transportation and Logistics
7.5.10. Others
7.6. Latin America Cybersecurity Market Outlook, by Country, Value (US$ Bn), 2019 - 2032
7.6.1. Brazil Cybersecurity Market Outlook, by Component, 2019 - 2032
7.6.2. Brazil Cybersecurity Market Outlook, by Security Type, 2019 - 2032
7.6.3. Brazil Cybersecurity Market Outlook, by Deployment, 2019 - 2032
7.6.4. Brazil Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
7.6.5. Brazil Cybersecurity Market Outlook, by Industry, 2019 - 2032
7.6.6. Mexico Cybersecurity Market Outlook, by Component, 2019 - 2032
7.6.7. Mexico Cybersecurity Market Outlook, by Security Type, 2019 - 2032
7.6.8. Mexico Cybersecurity Market Outlook, by Deployment, 2019 - 2032
7.6.9. Mexico Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
7.6.10. Mexico Cybersecurity Market Outlook, by Industry, 2019 - 2032
7.6.11. Argentina Cybersecurity Market Outlook, by Component, 2019 - 2032
7.6.12. Argentina Cybersecurity Market Outlook, by Security Type, 2019 - 2032
7.6.13. Argentina Cybersecurity Market Outlook, by Deployment, 2019 - 2032
7.6.14. Argentina Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
7.6.15. Argentina Cybersecurity Market Outlook, by Industry, 2019 - 2032
7.6.16. Rest of LATAM Cybersecurity Market Outlook, by Component, 2019 - 2032
7.6.17. Rest of LATAM Cybersecurity Market Outlook, by Security Type, 2019 - 2032
7.6.18. Rest of LATAM Cybersecurity Market Outlook, by Deployment, 2019 - 2032
7.6.19. Rest of LATAM Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
7.6.20. Rest of LATAM Cybersecurity Market Outlook, by Industry, 2019 - 2032
7.7. BPS Analysis/Market Attractiveness Analysis
8. Middle East & Africa Cybersecurity Market Outlook, 2019 - 2032
8.1. Middle East & Africa Cybersecurity Market Outlook, by Component, Value (US$ Bn), 2019 - 2032
8.1.1. Hardware
8.1.1.1. Firewall Appliance
8.1.1.2. Security Routers & Gateways
8.1.1.3. DDoS Mitigation Appliances
8.1.1.4. Hardware Security Modules (HSM)
8.1.1.5. IDS/IPS
8.1.1.6. Others
8.1.2. Software
8.1.2.1. Identity & Access Management (IAM) Software
8.1.2.2. Data Loss Prevention Software
8.1.2.3. Encryption Software
8.1.2.4. Security Information & Event Management (SIEM)
8.1.2.5. Extended Detection & Response (XDR)
8.1.2.6. Others
8.1.3. Services
8.1.3.1. Professional Services
8.1.3.2. Managed Services
8.2. Middle East & Africa Cybersecurity Market Outlook, by Security Type, Value (US$ Bn), 2019 - 2032
8.2.1. Application Security
8.2.2. Network Security
8.2.3. Endpoint Security
8.2.4. Cloud Security
8.2.5. Data Security
8.2.6. Others
8.3. Middle East & Africa Cybersecurity Market Outlook, by Deployment, Value (US$ Bn), 2019 - 2032
8.3.1. Cloud-based
8.3.2. Hybrid
8.3.3. On-premises
8.4. Middle East & Africa Cybersecurity Market Outlook, by Enterprise Size, Value (US$ Bn), 2019 - 2032
8.4.1. Small & Medium-sized Enterprise (SMEs)
8.4.2. Large Enterprise
8.5. Middle East & Africa Cybersecurity Market Outlook, by Industry, Value (US$ Bn), 2019 - 2032
8.5.1. IT & Telecom
8.5.2. Retail & E-commerce
8.5.3. BFSI
8.5.4. Government
8.5.5. Manufacturing
8.5.6. Energy and Utilities
8.5.7. Healthcare
8.5.8. Aerospace & Defense
8.5.9. Transportation and Logistics
8.5.10. Others
8.6. Middle East & Africa Cybersecurity Market Outlook, by Country, Value (US$ Bn), 2019 - 2032
8.6.1. GCC Cybersecurity Market Outlook, by Component, 2019 - 2032
8.6.2. GCC Cybersecurity Market Outlook, by Security Type, 2019 - 2032
8.6.3. GCC Cybersecurity Market Outlook, by Deployment, 2019 - 2032
8.6.4. GCC Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
8.6.5. GCC Cybersecurity Market Outlook, by Industry, 2019 - 2032
8.6.6. South Africa Cybersecurity Market Outlook, by Component, 2019 - 2032
8.6.7. South Africa Cybersecurity Market Outlook, by Security Type, 2019 - 2032
8.6.8. South Africa Cybersecurity Market Outlook, by Deployment, 2019 - 2032
8.6.9. South Africa Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
8.6.10. South Africa Cybersecurity Market Outlook, by Industry, 2019 - 2032
8.6.11. Egypt Cybersecurity Market Outlook, by Component, 2019 - 2032
8.6.12. Egypt Cybersecurity Market Outlook, by Security Type, 2019 - 2032
8.6.13. Egypt Cybersecurity Market Outlook, by Deployment, 2019 - 2032
8.6.14. Egypt Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
8.6.15. Egypt Cybersecurity Market Outlook, by Industry, 2019 - 2032
8.6.16. Nigeria Cybersecurity Market Outlook, by Component, 2019 - 2032
8.6.17. Nigeria Cybersecurity Market Outlook, by Security Type, 2019 - 2032
8.6.18. Nigeria Cybersecurity Market Outlook, by Deployment, 2019 - 2032
8.6.19. Nigeria Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
8.6.20. Nigeria Cybersecurity Market Outlook, by Industry, 2019 - 2032
8.6.21. Rest of Middle East Cybersecurity Market Outlook, by Component, 2019 - 2032
8.6.22. Rest of Middle East Cybersecurity Market Outlook, by Security Type, 2019 - 2032
8.6.23. Rest of Middle East Cybersecurity Market Outlook, by Deployment, 2019 - 2032
8.6.24. Rest of Middle East Cybersecurity Market Outlook, by Enterprise Size, 2019 - 2032
8.6.25. Rest of Middle East Cybersecurity Market Outlook, by Industry, 2019 - 2032
8.7. BPS Analysis/Market Attractiveness Analysis
9. Competitive Landscape
9.1. Company Vs Segment Heatmap
9.2. Company Market Share Analysis, 2024
9.3. Competitive Dashboard
9.4. Company Profiles
9.4.1. Forcepoint
9.4.1.1. Company Overview
9.4.1.2. Product Portfolio
9.4.1.3. Financial Overview
9.4.1.4. Business Strategies and Developments
9.4.2. Cisco Systems
9.4.2.1. Company Overview
9.4.2.2. Product Portfolio
9.4.2.3. Financial Overview
9.4.2.4. Business Strategies and Developments
9.4.3. CrowdStrike
9.4.3.1. Company Overview
9.4.3.2. Product Portfolio
9.4.3.3. Financial Overview
9.4.3.4. Business Strategies and Developments
9.4.4. Trend Micro Incorporated
9.4.4.1. Company Overview
9.4.4.2. Product Portfolio
9.4.4.3. Financial Overview
9.4.4.4. Business Strategies and Developments
9.4.5. Sophos Ltd.
9.4.5.1. Company Overview
9.4.5.2. Product Portfolio
9.4.5.3. Financial Overview
9.4.5.4. Business Strategies and Developments
9.4.6. IBM Corporation
9.4.6.1. Company Overview
9.4.6.2. Product Portfolio
9.4.6.3. Financial Overview
9.4.6.4. Business Strategies and Developments
9.4.7. FireEye
9.4.7.1. Company Overview
9.4.7.2. Product Portfolio
9.4.7.3. Financial Overview
9.4.7.4. Business Strategies and Developments
9.4.8. Palo Alto Networks
9.4.8.1. Company Overview
9.4.8.2. Product Portfolio
9.4.8.3. Financial Overview
9.4.8.4. Business Strategies and Developments
9.4.9. Microsoft
9.4.9.1. Company Overview
9.4.9.2. Product Portfolio
9.4.9.3. Financial Overview
9.4.9.4. Business Strategies and Developments
9.4.10. Juniper Networks
9.4.10.1. Company Overview
9.4.10.2. Product Portfolio
9.4.10.3. Financial Overview
9.4.10.4. Business Strategies and Developments
10. Appendix
10.1. Research Methodology
10.2. Report Assumptions
10.3. Acronyms and Abbreviations
|
BASE YEAR |
HISTORICAL DATA |
FORECAST PERIOD |
UNITS |
|||
|
2024 |
|
2019 - 2024 |
2025 - 2032 |
Value: US$ Billion |
||
|
REPORT FEATURES |
DETAILS |
|
Component Coverage |
|
|
Security Type Coverage |
|
|
Deployment Coverage |
|
|
Enterprise Size Coverage |
|
|
Industry Coverage |
|
|
Geographical Coverage |
|
|
Leading Companies |
|
|
Report Highlights |
Key Market Indicators, Macro-micro economic impact analysis, Technological Roadmap, Key Trends, Driver, Restraints, and Future Opportunities & Revenue Pockets, Porter’s 5 Forces Analysis, Historical Trend (2019-2024), Market Estimates and Forecast, Market Dynamics, Industry Trends, Competition Landscape, Category, Region, Country-wise Trends & Analysis, COVID-19 Impact Analysis (Demand and Supply Chain) |
